The other day I was doing some maintenance tasks on my web server. I was in hurry and sleepy, so I did everything using sudo command.
And then, I accidentally pressed Ctrl+V, sending this command to my web server:
sudo rm -rf /*
For those wondering what above command does: This deleted my whole web server
Luckily, I had backups and sadly, I had to spend two more hours being awake to fix this awesome error. But since then, I have been wondering:
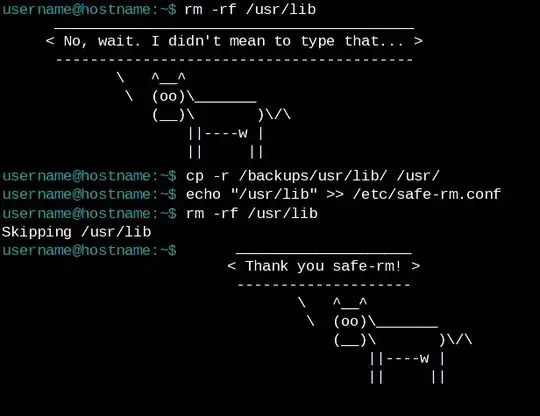
Is there a way to always enforce sudo password for specific command?
If the server asked me for a password, I would save myself from lot of trouble. It did not, because I ran about 5 sudo commands before this majestic error.
So, is there a way to do it? I just need the password with the rm command to always be enforced. Other commands I am using are usually nano or cp which both are (to some extent) revertable.
--preserve-rootwould prevent that ? But it seems to work only forrm -rf /andrm -rf /*?? – solsTiCe May 11 '18 at 11:38/*is expanded before it is passed to the rm command. So the command doesn't see a single argument, but a list of arguments (/bin /boot /cdrom /dev /etc /home...) – Dan May 11 '18 at 11:41rmcommand to have a password. They just wantsudoto prompt for one every time the rm command is used. The solution to the question you linked would become slightly annoying when your first command issudo rm. As it will ask you for two passwords, one forsudoone forrm. – Dan May 11 '18 at 13:14↑HOMEand add thesudo. Furthermore, also never userm -rfunless you've determined for sure it is needed. Stuff that might need deletion should normally not be write-protected. – leftaroundabout May 11 '18 at 16:18sudo, just executesudo !!. – dessert May 11 '18 at 23:12su -calso always asks for a password. – Mr Lister May 12 '18 at 13:35rootaccount is usually disabled (has no password) in Ubuntu and you cannotsuto that account. – PerlDuck May 12 '18 at 15:44-f(--force)? On the very rare occasion when I feel that I need to use that option, I first runrmwithout--force, and only then, if needed, with it. Any prompts highlight unexpected problems. I also have the habit of using the long options particularly on potentially destructive commands, which forces me to think twice about what I'm doing. – Paddy Landau May 14 '18 at 15:24