I want a portable version of Ubuntu that I can easily carry in my pocket. Problem is that I need it to be encrypted or it's useless. Every set of USB stick instructions I've seen so far does not account for the ease with which one might loose a USB stick. This seems like a major issue to me. How do we claim that Ubuntu is secure, if it isn't? The average person can't even keep track of their laptops and notebooks. How are they going to keep track of a USB stick?? ...and then having lost it, instantly have a major security breach?
-
LOL. Someone that cares about security stays away from USB sticks and uses a VPN with 2 or 3 way authentication."How do we claim that Ubuntu is secure, if it isn't?" what does that claim have to do with USB sticks?! Nothing. "and then having lost it, instantly have a major security breach? " My USB sticks contain ZERO client related data not does it contain passwords or ssh keys as this is a breach of the privacy laws in The Netherlands if a stick is stolen. – Rinzwind Jan 14 '19 at 11:27
-
My passwords are in a safe and my ssh keys I fetch from an instance where i need to call someone to make them available. – Rinzwind Jan 14 '19 at 11:29
-
- I don't keep ANY client related data on my personal machines. 2. My passwords are generated using an assortment of things. I don't need to secure them because you literally have to be me to know the things. Also it's not necessarily the same things for each password. Items are randomly selected from the list of things. There's more to this that I won't discuss. Security. ;-)
– NonYaBidnezz Jan 14 '19 at 12:49
3 Answers
Where can I find instructions for a portable USB Stick version of Ubuntu that is encrypted?
You can use the same instructions for any encrypted partition for Ubuntu if you want to encrypt using tools available for Linux/Ubuntu. All you need to take care of is to point to the correct device that needs encrypting. And you can do that with the "disks" option from dash.
If you want instructions based on images the ubuntuhandbook has a guide.
The command line method is shorter:
cryptsetup -v --verify-passphrase luksFormat /dev/{device}
cryptsetup luksOpen /dev/{device} backup
mkfs.ext4 /dev/mapper/backup
cryptsetup luksClose /dev/mapper/backup
where {device} is the device you want encrypted.
Mind though that encryption is not really security; it is security by obscurity. It stops some users from accessing the data but there are ways to retrieve the passphrase (a sharp knife for instance).
- 299,756
If you accept, that every encrypted system can be cracked, you can create an installed system in a USB drive (a fast USB 3 pendrive or USB SSD).
It is easy to install (like installed into an internal drive, but into a USB drive),
if you unplug the internal drive
when booted from a normal live Ubuntu system in another USB drive
run Ubuntu's standard installer (
ubiquity)at the partitioning page, select LVM with encryption (which is LUKS encryption)
continue like it were a normal installation.
This link may help: How do I install Ubuntu to a USB key? (without using Startup Disk Creator)
- 46,324
- 5
- 88
- 152
-
Yes. Locks are for keeping honest people honest. A dishonest person will drive a stolen pickup truck into your living room to get your things. We still use locks though because they work, i.e. they discourage a certain amount of illicit activity just like walls, fences and encryption which we also still use for the same reasons. – NonYaBidnezz Jan 14 '19 at 12:38
-
I believe that Full Disk Encryption only started working with USB installs using Ubuntu 18.04 and later. With previous versions, (16.04), only encrypted home works with USB. – C.S.Cameron Jan 16 '19 at 06:13
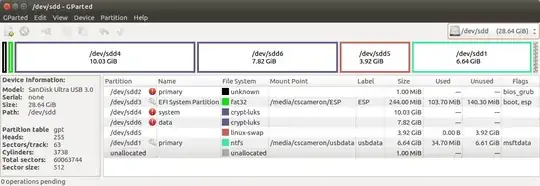
BIOS/UEFI Flash Drive with Full Disk Encryption
I have been playing with Paddy Landau's Manual Full System Encryption: https://ubuntuforums.org/showthread.php?t=2399092
Out of the box the script works UEFI only.
With a mkusb base, almost anything BIOS/UEFI is possible.
Start with a default mkusb Live install to flash drive (4GB or larger).
Next create a mkusb Persistent install to flash drive using defaults (16GB or larger).
As soon as mkusb finishes with the persistent install, open gparted and delete sdx4 and sdx5.
Refer to https://help.ubuntu.com/community/ManualFullSystemEncryption.
Follow Item 6.4-Detailed process: https://help.ubuntu.com/community/ManualFullSystemEncryption/DetailedProcess.
Complete Item 4.2.1 Creating new partitions sdx4-system, sdx5-swap* and sdx6-data*.
Boot the Live USB in UEFI mode.
Complete Item 4.2.2-Prepare for the Installer, and start the installer.
Run the installer per item 4.2.3-Install Ubuntu.
At this point the flash drive will be UEFI only.
- Now mount the ESP boot partition and copy ESP/EFI/ubuntu/grub.cfg and overwrite ESP/boot/grub/grub.cfg.
Your Bootable flash drive will now have encrypted system, home and swap files and will boot either BIOS or UEFI.
Notes:
- *Separate home, swap and NTFS partitions are optional.
- Many people recommend against using swap with a bootable USB or SSD for fear of wear.
- The swap partition, if used, can be encrypted using ecryptfs-utils.
- The NTFS partition, if used, can be encrypted using VeraCrypt so that it can be used in both Linux and Windows.
- If there are problems reusing the installer drive on a second encrypted install, confirm /mnt/root/ has been deleted and that the correct UUID for sdx3 has been used in fstab.
- GParted on the encrypted drive may not work.
- 19,519