As a noob to Linux I do not know if it is possible to encrypt whole drive with current calamares installer
I did a fresh install of Lubuntu with these options in calamares
erase disk +encrypt system
When rebooting it asks :
Welcome to GRUB! Attempting to decrypt master key...
Enter passphrase for hd0
After decrypting I have only to log in as user
Normally we have to put password under Lubuntu logon
Is in this case the complete system encrypted ? Is the grub prompt normal ?
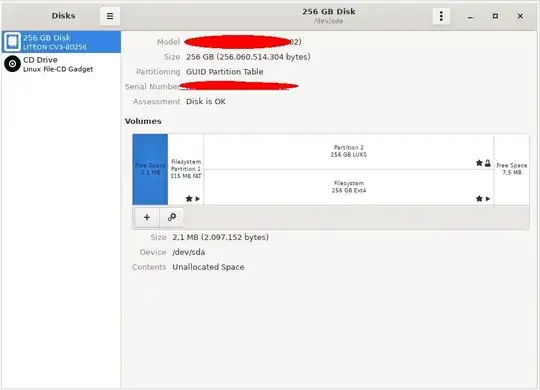
Here is the output of lsblk
sda 8:0 0 238,5G 0 disk
├─sda1 8:1 0 300M 0 part /boot/efi
└─sda2 8:2 0 238,2G 0 part
└─luks-5fc-xx-xxx-xxxx-xxx
253:0 0 238,2G 0 crypt /
sr0 11:0 1 3,7M 0 rom /media/
/bootis encrypted, yes. It's part of/. From what you have posted you don't have a separate boot partition. You have a efi partition, which has to be unencrypted. – vidarlo Jun 18 '19 at 18:34/boot/efi*has* to be unencrypted. You currently have no separate/bootpartition. – vidarlo Jun 18 '19 at 18:49