I've been working on a solution to this for weeks, and I'm about to say screw it and write a python app that can actually block IP addresses, because so far nothing seems to work like it's supposed to.
/etc/hosts can't block a range of IP addresses, nor can it block the URL I'm trying to block,
and there doesn't seem to be a decent GUI that can manage iptables locally without insecurities like ssh (fwbuilder) that isn't unavailable (firestarter).
So I'm stuck to using gufw which in itself doesn't want to work:

The site shown is an ad cdn I'm trying to block for an app I use. (the log is empty)
I think I'm starting to understand why every search I do refers to cumbersome terminal solutions like ufw or iptables...
Is there any way to actually get gufw to work like it's supposed to??
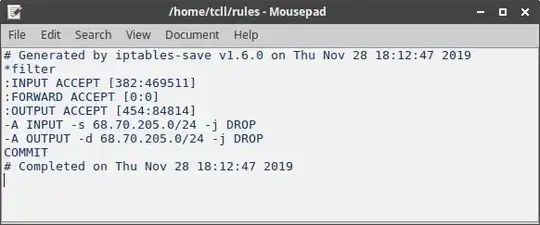
/etc/hostsyou add the line and make it go toloopback (127.0.0.1)or0.0.0.0so the entry looks like127.0.0.1 a-us00-kxcdn.com. That way when the app tries to make the call back to the ad it is routed to127.0.0.1instead. – Terrance Nov 27 '19 at 23:360.0.0.0), though honestly most seem to recommend iptables over/etc/hostsanyways, and I've used it before (it's quite a hassle) so I know it works better. – Tcll Nov 27 '19 at 23:40piholeto block ads. – Terrance Nov 27 '19 at 23:51127.0.0.1 68.70.205.#for however many entries I had to add, although that stopped working when I got to .30 – Tcll Nov 28 '19 at 00:10kxcdn.cominstead. I have been looking at the blocking hosts files I have and a lot of them are blocking the domains that are involved instead of individual hosts. I have mine using thednsmasqsince it is capable of loading as many hosts files as I want. Right now my router which runs Linux is blocking just over 63,000 sites. – Terrance Nov 28 '19 at 01:30kxcdn.comactually has a completely different IP that doesn't actually show up in wireshark when the ad requests are made... although I'd only blocked the url and not the ip... still though, I have the68.70.205.xxIP blocked, meaning I should be seeing requests (maybe) with no responses... I'm actually not sure if wireshark would display the blocked requests, since I assume it catches them before they're blocked... – Tcll Nov 28 '19 at 01:47