Using virt-manager, KVM on Ubuntu, I created a VM with default network configuration (NAT) as described here: https://wiki.libvirt.org/page/VirtualNetworking under NAT mode.
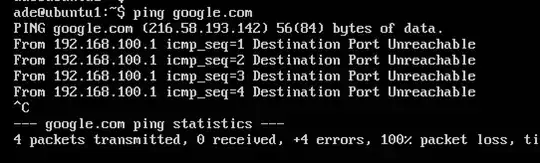
which should have internet connectivity by default. But I am unable to ping internet addresses from the VM. instead, I am getting destination port unreachable from the corresponding host interface
I am suspecting it is something to do with iptables 'reject-with icmp-port unreachable' configurations in the forwarding table below. The rules were atomatically created by virt manager, but even when I remove the rules, I still get the same problem. any ideas please
Chain FORWARD (policy ACCEPT)
num target prot opt source destination
1 ACCEPT all -- anywhere 192.168.150.0/24 ctstate RELATED,ESTABLISHED
2 ACCEPT all -- 192.168.150.0/24 anywhere
3 ACCEPT all -- anywhere anywhere
4 REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
5 REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
6 ACCEPT all -- anywhere 192.168.100.0/24 ctstate RELATED,ESTABLISHED
7 ACCEPT all -- 192.168.100.0/24 anywhere
8 ACCEPT all -- anywhere anywhere
9 REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
10 REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
11 ACCEPT all -- anywhere anywhere
12 ACCEPT all -- anywhere anywhere
13 ACCEPT all -- anywhere anywhere
14 DOCKER-USER all -- anywhere anywhere
15 DOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
16 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
17 DOCKER all -- anywhere anywhere
18 ACCEPT all -- anywhere anywhere
19 ACCEPT all -- anywhere anywhere
and NAT rules
Chain POSTROUTING (policy ACCEPT)
num target prot opt source destination
1 RETURN all -- 192.168.150.0/24 base-address.mcast.net/24
2 RETURN all -- 192.168.150.0/24 255.255.255.255
3 MASQUERADE tcp -- 192.168.150.0/24 !192.168.150.0/24 masq ports: 1024-65535
4 MASQUERADE udp -- 192.168.150.0/24 !192.168.150.0/24 masq ports: 1024-65535
5 MASQUERADE all -- 192.168.150.0/24 !192.168.150.0/24
6 RETURN all -- 192.168.100.0/24 base-address.mcast.net/24
7 RETURN all -- 192.168.100.0/24 255.255.255.255
8 MASQUERADE tcp -- 192.168.100.0/24 !192.168.100.0/24 masq ports: 1024-65535
9 MASQUERADE udp -- 192.168.100.0/24 !192.168.100.0/24 masq ports: 1024-65535
10 MASQUERADE all -- 192.168.100.0/24 !192.168.100.0/24
11 MASQUERADE all -- 172.17.0.0/16 anywhere
12 MASQUERADE all -- 192.168.122.0/24 anywhere
13 MASQUERADE all -- 192.168.223.0/24 anywhere
Thanks,
sudo iptables -v -x -n -Landsudo iptables -t nat -v -x -n -L. – Doug Smythies Feb 08 '20 at 16:54