I just read a description of CVE-2020-1971, which indicates that a patch was released today for openSSL, the patched version is 1.1.1i -- my version of Ubuntu 20.04.1 LTS is running openSSL version 1.1.1f. From last March.
Software Updater says that my system is up to date. I am hoping that this openSSL update is released by Canonical by tomorrow... can anyone confirm they are working on this?
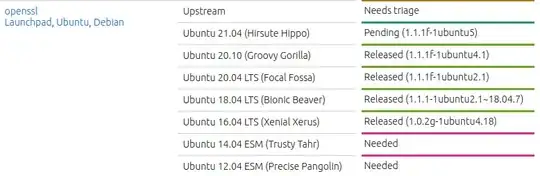

apt updatebefore listing available versions withapt listor trying an upgrade withapt install. In this particular case:apt list openssl --installedreturns:openssl/now 1.1.1f-1ubuntu2 amd64 [installed,local]whileapt update && apt list openssl --installedreturns:openssl/focal,now 1.1.1f-1ubuntu2 amd64 [installed,upgradable to: 1.1.1f-1ubuntu2.1]– mirekphd Dec 25 '20 at 12:14