First, you need to know that there are TWO ways to fix a vulnerability: Upgrading and Patching.
- Upstreams emphasize "upgrade" in their public announcements simply because most folks don't know how to patch. But both methods are long-accepted practices.
- Ubuntu (and many other distros) prefer to patch because upgrading can introduce new bugs and regressions. Upstreams usually make patches available specifically for this purpose.
This means that a fully-secure openssl package in Ubuntu WON'T be version 3.0.7. That's why we need to know the specific CVE(s) for the vulnerabilities.
Second, lets find those CVE(s). A bit of search-engine-fu reveals that the OpenSSL 3.0.7 release targets two CVEs:
- CVE-2022-3602
- CVE-2022-3786
Third, let's look at CVE-2022-3602 in the Ubuntu CVE Tracker:
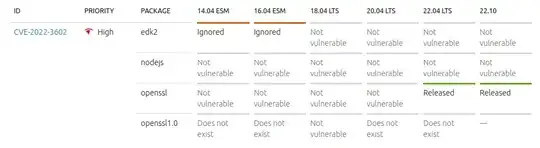
This tells us a couple of important things:
- The Ubuntu Security Team is already tracking the issue.
- The only package affected is
openssl.
- A patched package has already been released.
Fourth, let's dig a little deeper by looking at package details the tracker:

Now we know the exact version numbers of openssl packages that are patched and secure.
- Reminder: It's patched, so the version number is NOT 3.0.7. But it's still secure; that CVE has been mitigated.
Finally, let's see if our 22.04 system has that secure package version
$ apt list openssl
Listing... Done
openssl/jammy-updates,jammy-security,now 3.0.2-0ubuntu1.6 amd64 [installed,automatic]
It's not the secure version (recall that the secure version is 3.0.2-0ubuntu1.7). But it was released today, so a simple sudo apt update and sudo apt upgrade shows an openssl update, then:
$ apt list openssl
Listing... Done
openssl/jammy-security,now 3.0.2-0ubuntu1.7 amd64 [installed,automatic]
SECURE! This system is now running a package that has been patched by the Ubuntu Security Team to mitigate CVE-2022-3602.
Checking if CVE-2022-3786 is also mitigated is left as an exercise for the student.
One final note: If a lot of this information was new to you (patching, CVEs, tracker, confusing version numbers), then one easy way to pierce the veil and understand what's going on is a couple episodes of the Ubuntu Security Podcast, a short weekly discussion of security-related topics from the Ubuntu Security Team. They want you to understand it!


apt policy <package-name>, you'll get info if there is an updated package. – Artur Meinild Nov 01 '22 at 18:22