When a USN is posted, that means an update for all affected versions has been released to the repository in both -security and -updates pocket for the affected releases, and most likely for every release thereafter, especially if it's fixed by the upstream developers for a given source pacakge.
This is where you have to look at the CVE page itself for a given CVE to really start to dissect this, and also have a little bit of understanding how Ubuntu package versions are determined among other things. This is the CVE tracker page for the CVE you've referenced (CVE-2017-6519).
When a security update is pushed it lands in both -security and -updates pockets. This is done to make sure all people get the security patch.
However, you have to do version comparisons of the package versions you have installed vs. the affected/fixed versions.
This is the screenshot of this page right now:

We can see that the first version in Ubuntu to receive this fix was 0.7-3.1ubuntu1.2, which was introduced in Bionic.
We then refer to the versions in your system - 0.7-4ubuntu7.2. This is the same codebase as 0.7-3.1ubuntu1.2 - that is Avahi 0.7 - but with additional package revisions and patches.
Because these are the same code base version but different package revisions that're later than the "fix released" version, you are already patched for this CVE. That's why later releases don't show up in the table, and why you don't need to worry. Later versions of Avahi are likely fixed and patched for this CVE as well.
Avahi has actually patched this in version 0.8 from Upstream. We know this from their github tags and release notes - https://github.com/lathiat/avahi/releases/tag/v0.8
As such, the CVE needs updated to reflect the Upstream patch version to mark that as released/fixed. However, your codebase is 0.7, so the version of the package in your release of Focal is built off that package with additional packaging changes to get to -4ubuntu* as its package version string.
We can see all the versions of Avahi available by looking at its page in Launchpad for what supported releases there are and what versions each release has:
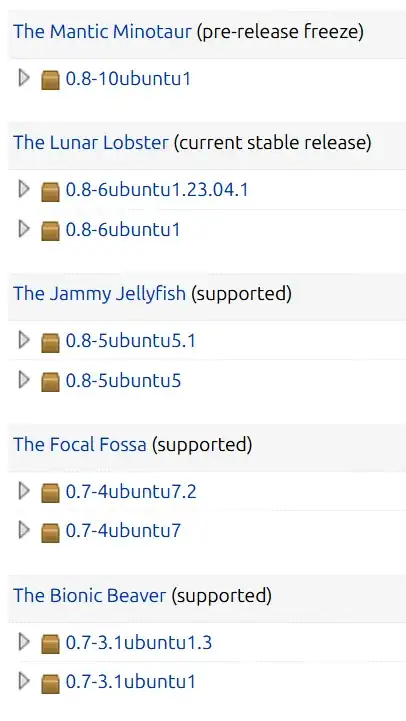
The Security team once they publish a fix is not obligated to go back and update the tracker for upstream's patch versions, though they do sometimes do that it doesn't always get updated (in this case I asked the Security team to update that CVE's page).
Because this security patch was fixed in version 0.8 of Avahi, you will note all later versions of Ubuntu are using version 0.8 and as such already have this patch included (and not distro-patched in the -security repos for those later releases but included as part of the base code for Avahi).

