As a member of the Community Council and as an Ubuntu Developer myself, I reached out to Debian and Ubuntu security contacts.
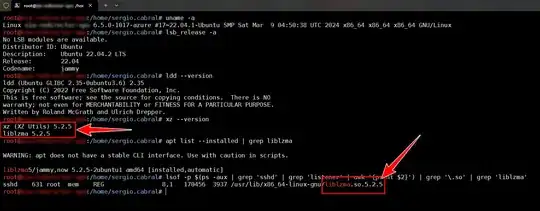
LTS and currently stable releases of Ubuntu do not have versions of xz that are affected by this, so existing Ubuntu releases are unaffected.
The impacted xz versions were only in noble-proposed which impacts only the in-development release. No versions of xz in already-released versions of Ubuntu are affected.
The in-development release, Noble 24.04, is currently being deep-dived and scoured for whether there is any lasting effect, and both Debian and Ubuntu reverted the packaging to a known-good older xz release that does NOT contain revisions from the malicious actor.
The Ubuntu Security Team is still tracking this, though no impact exists on current stable releases (Noble is not yet released at the time of this post, so it is not considered 'stable'.)