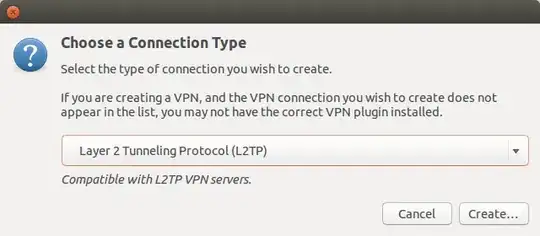
Previously, I was trying to figure out how to install the L2TP/IPSEC manager code. I guess Ubuntu/Canonical switched away from OpenSwan to StrongSwan, but didn't really announce it. So that was figured out in this AskUbuntu question: L2TP IPsec VPN client on Ubuntu 14.10
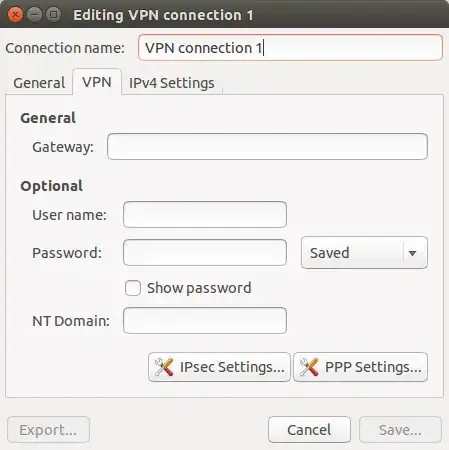
Since then, I've been trying to figure out how to use Pre-Shared Keys for Authentication to the Server. As shown in the screenshot, the Network Manager allows for a Certificate (.pem file), but not a Pre-shared key.
My network admin doesn't want to mess around with Certs because PSKs are good enough for the situation we're working with. I've already tested these PSKs with Windows and they work great.
He's given me 4 pieces of info.
- Server name
- PSK for said server
- User name
- password for said username
I can see on this screenshot where to put the server name and username, but cannot see where to put the PSK for the server, nor where to enter the password (maybe I'm prompted for that at connection time.)
Anyone know how to do this?
UPDATE: So I tried hackerb9's suggestion, but it didn't appear to do anything. I also tried alci's suggestion of downloading the 1.3.1 version of Network-Manager for L2TP and compiling manually. After installing a bunch of packages and re-running ./configure a few times, I eventually was able to "make" and then "make install" the code.
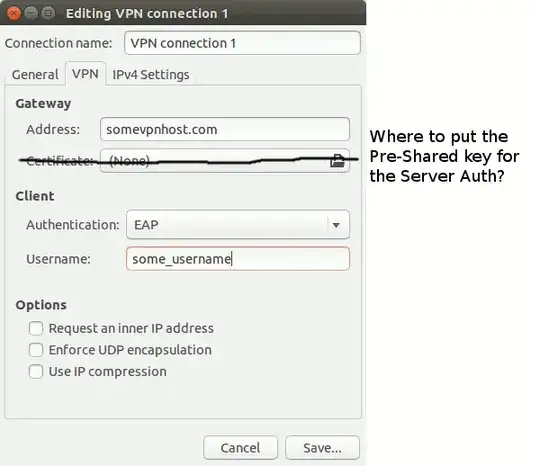
The plug-in for network manager now shows a Pre-shared Key option, but it still doesn't work. It now looks like this:

The problem with this is that the "Certificate" option is still being displayed (instaed of the Pre-shared key field.)
Where in this Ubuntu Network Manager plugin am I supposed to enter the Pre-shared Key for Server authentication?
As an example for contrast, in Windows 8, it has an option that looks like this: