A standard installation of Wireshark doesn't give the program permission to access the network interface.
I suppose I have to run the program with sudo, but do not know how to add it to the icon - if that's the way to do it.
A standard installation of Wireshark doesn't give the program permission to access the network interface.
I suppose I have to run the program with sudo, but do not know how to add it to the icon - if that's the way to do it.
For WireShark there's a better way. The bit that normally needs root is the packet collection application and this can be configured to allow certain people to use it without sudo, gksu, etc.
In a terminal (very important that you're in a terminal, not just the Alt+F2 dialogue) run this:
sudo dpkg-reconfigure wireshark-common
This will ask you if you want to allow non-root user to be able to sniff. That's what we're aiming for, so select Yes and hit return.
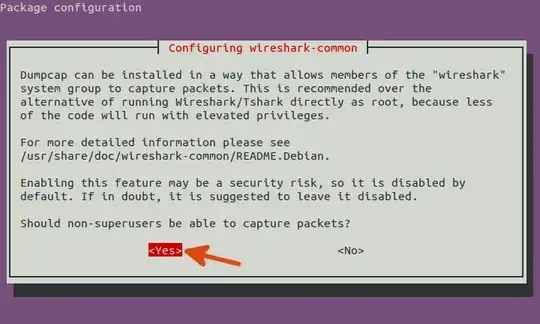
This adds a wireshark group. Anybody in that group will be able to sniff without being root. This is obviously more secure than just letting anybody sniff but does mean there's no password checking. Technically any person with access to a computer logged in with a wireshark account will be able to sniff. If that's acceptable to you, carry on.
If not, run that again and select no.
Then you just need to add the user to that group. Run this:
sudo adduser $USER wireshark
And restart or log out. When you're back in it should let you start sniffing without any fuss about being root.
newgrp wireshark command to temporarily enter the group after you have become a member of the wireshark group.
– Lekensteyn
Mar 14 '17 at 14:25
su - $USER as described at Reload a Linux user's group assignments without logging out - Super User
– nealmcb
Apr 13 '17 at 02:56
newgp command changes your primary group id. That denied me access to key mounted filesystems. Much more reliable to use su - username.
– will
Sep 24 '19 at 04:53
Really you do not need to launch WireShark as root. Please read official page. In brief you should do:
sudo groupadd wireshark
sudo usermod -a -G wireshark $USER
sudo chgrp wireshark /usr/bin/dumpcap
sudo chmod o-rx /usr/bin/dumpcap
sudo setcap 'CAP_NET_RAW+eip CAP_NET_ADMIN+eip' /usr/bin/dumpcap
sudo getcap /usr/bin/dumpcap
Then log-out and log-in again.
Note: this method was tested on 16.04 LTS, 17.10 and 18.04 LTS.
You can also run Wireshark with root privileges by running gksu wireshark from the terminal.
Note that there are security concerns with running Wireshark in this mode, namely that any exploit that compromises Wireshark now has root privileges rather than user privileges. This is more of a concern with Wireshark than other application because, by it's very nature (capturing and processing arbitrary input), Wireshark is more vulnerable to exploits than typical desktop applications. You are probably safe on a SOHO network, but you should be aware of this concern before proceeding.
Citations:
tcpdumptool in Linux ifwiresharkis giving you too much troubles. – warfreak92 Nov 15 '17 at 15:24sudo dpkg-reconfigure wireshark-commonselect yes then:sudo chmod +x /usr/bin/dumpcap– EsmaeelE Apr 07 '20 at 20:08