So we have some remote workers who are required to have full disk encryption by policy. Recently I had an issue where someone removed the administrator privileges such that no administrators were left for that machine and we aren't using SSO for contextual reasons that aren't relevant to the issue. So the question is, if you have full disk encryption set up, how do you rescue the box? I'm specifically referring to booting in at runlevel 1 so we can give admin rights to at least one user.
-
1"It can't be done." would be an acceptable solution if it can't be done. ;-) – user447607 Oct 03 '16 at 13:41
-
How about booting into recovery mode then drop to shell, did you tried it? – user.dz Oct 03 '16 at 21:12
-
Hey, thanks for answering! :-) I'll try it but I doubt it would work. Seems like the password prompt comes before the Grub screen. Will test though. – user447607 Oct 15 '16 at 14:27
1 Answers
I did recently rescue a box with full disk encryption and no administrator. I did so by adapting the following anwser How do I reset a lost administrative password?
Ps : I don't have enough reputation to include images, it would be nice if someone could edit and add them inline :)
Full steps :
You need to boot into recovery mode.
Boot up the machine, and after the BIOS screen, hold down the left Shift key. You will then be prompted by a menu that looks something like this:
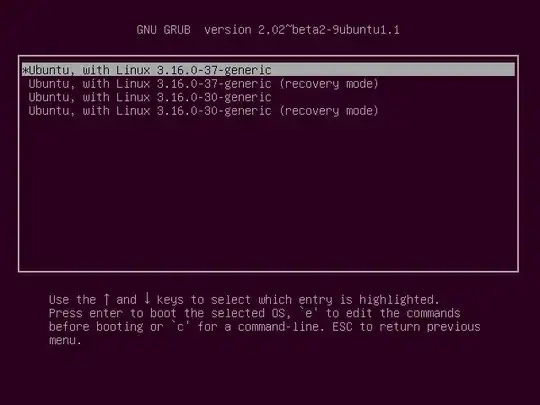
I've noticed on some systems that timing when to hit the left Shift key can be tricky, sometimes I miss it and need to try it again.
As you have full disk encryption, you have to hold down the key before being asked for the disk password. (You will be asked for the password in a command line interface during boot).
Hit the down arrow until you select the 2nd entry from the top (the one with the recovery mode in the description) and then hit Enter.
Now you should see this menu:

Using the arrow keys scroll down to root and then hit Enter.
You should now see a root prompt, something like this:
root@ubuntu:~#
At this stage you should have a read-only filesystem. You have to remount it with write permissions:
mount -o rw,remount /
Now we can set the user back into the sudoers group with the adduser command. (In this example I will use jorge as the example, you need to substitute whatever the user's username is):
root@ubuntu:~# adduser jorge sudo
Now you can reboot, and you should be able to use sudo commands. You might want to make sure that you are part of following groups :
- adm
- sudo
- lpadmin
- sambashare
- jorge (your username)
jorge@ubuntu:~$ groups
You can add your user back in these groups with sudo
jorge@ubuntu:~$ sudo adduser jorge adm
- 151
- 1
- 4