The computer aspect
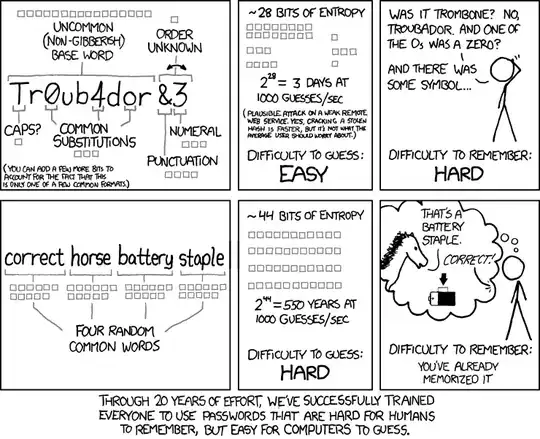
Use a method, that provides sufficient randomness alias entropy, often measured in bits.
Accept the first offered choice from the random process. Otherwise the entropy decreases (often more than you would think), and your security level will be lower.
The human aspect
Considering the human aspect it is important that you can
the words in the password/passphrase.
In order to preserve randomness, entropy, it is very important the you accept the first offered choice, and the word list can make a difference.
Using a big word-list provides more entropy per word, but chances are that you or users in the group, whose IT security you are managing, refuse to use the first offered password/passphrase. Your name, city or other personal data might be selected from the word list in an extremely rare case, but more often you might be offended by a political, ethnical, religious, sexual or generally rude word. Of course, if you like such words, you can add them to your own word list ;-) but don't force them onto other people.
It will make it easier to accept, remember and spell the password/passphrase, if you use a list of the most common words, where the words are selected for this particular purpose.
Create a word list yourself
You can create such a list yourself (and in your own language, and remove words with special characters, because they might cause problems with some software).
The following shellscript pruner might help. You get only lowercase words, which makes the typing easier (special characters are removed) and only words in the interval [4,10] letters (not too short, not too long). But there is no sorting of these files according to how easy to accept they are. You need other information to remove uncommon, difficult and potentially offensive words, or you can do it manually.
#!/bin/bash
LANG=C
for wordlist in
$(find /usr/share/dict/ /usr/lib/python3/dist-packages/xkcdpass/static -type f -size +10k)
$(ls -1 word-list.txt 2> /dev/null)
do
prunedlist="${wordlist##*/}"
prunedlist="${wordlist////_}"
prunedlist="${prunedlist/.txt}-pruned.txt"
echo "source: $wordlist"
echo -n "Total number of words in list: "
< "$wordlist" wc -l
echo "target: $prunedlist"
echo -n "Used lower case words ( 4 < length < 10 ): "
< "$wordlist" tr -d '\015'|
grep '^[a-z]{4,10}$' |
tee "$prunedlist" |
wc -l
echo "-------"
done
The shellscript will find the default word lists and also word lists for xkcdpass and cracklib, if installed.
Now you can run your shuf command line to test the pruned word lists,
$ for i in *pruned*; do echo "$i:";shuf -n4 "$i"| awk NF=NF RS= OFS=' ';echo "-----";done
but I would prefer xkcdpass.
Download a word-list
You can download such a list (check that it consists of unique words and is long enough, at least 2048 words = 2^11 words, which corresponds to 11 bits of entropy).
Downloading, checking and using such a file from the internet should be safe. As usual, you should only use reliable web sites.
The important thing for the security is not the words themselves, but that you let a random process (for example dice) or a good pseudo-random computer process select the words. Do not tamper with the random process by selecting or modifying the password manually.
At this Ubuntu help wiki page: The XKCD method - xkcdpass you can find a
Custom word list - 'word-list.txt'
Useful command-lines with xkcdpass
Decide what works best for the security level you need in your particular case,
- lower number of words that are strange and complicated
- higher number of words that are common and easy
It may be vary between persons (and groups of people, if you are considering how to set a policy or custom tool for an organization).
You can let xkcdpass compute randomness alias entropy in bits by adding the verbosity option -V. These examples use the default word list and the custom word list from the Ubuntu help page word-list.txt,
xkcdpass -V -n 3
xkcdpass -V -n 4 --min 4 --max 10 -d . -w word-list.txt
Using the default word file: lower number of words that are strange and complicated
# Normal security level at home, entropy = 45 bits;
$ xkcdpass -n 3
demeanour basely extrude
Next security level, entropy = 60 bits:
$ xkcdpass -n 4
metal cottager advocacy soursop
High security level, entropy = 76 bits:
$ xkcdpass -n 5
hostile impounder Caledonia ramie Goddard
Very high security level, entropy = 91 bits:
$ xkcdpass
ambrosia Cossack vivify Barbudan royal Campinas
Please notice that this is the default setting. But the security level is very high only if the user
- can accept the first password/passphrase offered,
- can remember it without a post-it sticker on the monitor/laptop (or other 'shortcut'),
- can spell it without a post-it sticker on the monitor/laptop (or other 'shortcut').
Using a custom word file: higher number of words that are common and easy
# Normal security level at home, entropy = 47 bits:
$ xkcdpass -n 4 --min 4 --max 10 -d . -w word-list.txt
sharp.hockey.steal.backyard
Next security level, entropy = 59 bits:
$ xkcdpass -n 5 --min 4 --max 10 -d . -w word-list.txt
initially.assistant.barely.framework.regional
Next security level, entropy = 71 bits:
$ xkcdpass -n 6 --min 4 --max 10 -d . -w word-list.txt
snake.food.dress.perception.club.waste
High security level, entropy = 83 bits:
$ xkcdpass -n 7 --min 4 --max 10 -d . -w word-list.txt
stand.mentor.know.cream.automatic.treatment.effect
shufis using a good random generator before letting it create my passwords; 2. Ifshufis good, I would still prefer a word list, that is made for this purpose, for example the default list ofxkcdpassor the custom word list from https://help.ubuntu.com/community/StrongPasswords#Custom_word_listxkcdpassdoesn't allow (truly) custom wordlists… – dessert Nov 17 '17 at 20:24xkcdpasswith the option-wlike so:for i in *pruned*; do echo "$i:";xkcdpass -w "$i";echo "-----";doneand of course add other options too, to get more precisely the format I want. – sudodus Nov 17 '17 at 20:31