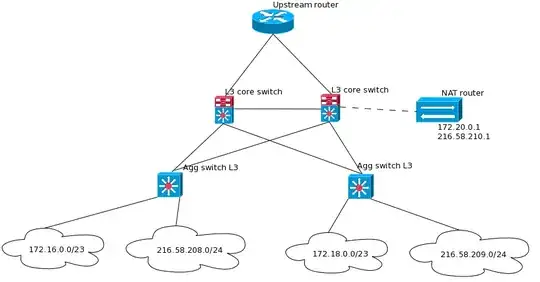
I will have a routed network with both public and private subnets routed with OSPF. There will be two core routers that both have a default route to the internet.
My question is how I make sure that no traffic with a private src-addr is routed outside my OSPF-area and also how I NAT this traffic. My idea right now is to have a specific NAT-router set up in the network and then do policy based routing on the core routers.
EDIT:
We are using L3 switches of different brands. The aggregation layer is mostly HP5400 and the core layer will be Dell S6000-ON. In the diagram you can see a simplyfied picture of our network. Right now we plan to have a dedicated NAT router (probably a linux machine) which lives on both private and public adresses to which we direct traffic from the core switches with PBR