Not sure if this is a good stack exchange site to post this on but here goes nothing,
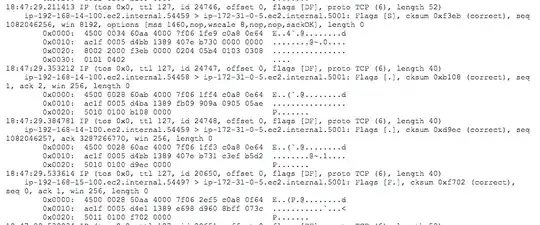
The problem, As you can see from my Wireshark screenshot the TCP handshake is not happening. The remote is sending me the SYN message but I'm not responding to SYN/ACK. I can connect just fine with my own socket client and watch the handshake work perfectly, the only difference being I'm not accessing our server through the VPN tunnel.
The backstory, is we've been tasked with connecting to a remote service (192.168.X.X) that is essentially a black box to us. Both systems are connected via an IPSec tunnel. Communication is supposed to be done through a TCP socket with our end (172.31.0.5) implemented in python acting as the server. All we know about their end is that it's running on Windows. Their end is configured with an IP and port, that's it.
Thank you for your time.