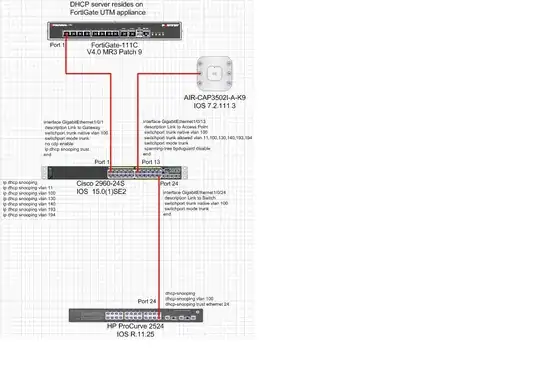
Have establsihed a lab to test IP DHCP SNOOPING prior to implemntation. So far everything works as advertised. Given that the Uplink port of a switch must be trusted, why is it not necessary to add the trust to a access point?
Asked
Active
Viewed 1,311 times
7
Mike Pennington
- 29,876
- 11
- 78
- 152
rsebastian
- 251
- 1
- 5
-
I don't understand what you are asking. Can you please elaborare? – Sander Steffann Aug 12 '13 at 15:48
-
for example port 24 trunk of the HP switch must have DHCP-SNOOPING TRUST applied no other ports on the switch would be able to respond to DHCP Discover packets from the clients. So even through the attacker has set up a rogue dhcp server, the port on the switch to which the attacker has connected would not be allowed to respond to DHCP discover packets. Could one not bring up DHCP after connecting wirelessly without the trust in place there? – rsebastian Aug 12 '13 at 16:29
-
Snooping has to follow the path towards the DHCP server. Port 24 on the Cisco should not need trust but port 24 on the HP needs to because that is the path towards the DHCP server. – Daniel Dib Aug 12 '13 at 17:12
-
I do agree with @DanielDib that you shouldn't trust port 24 on the Cisco generally speaking based on this diagram. However, if you don't plan to implement DAI or some other feature that requires the entries in the binding table, then you can trust port 24 on the Cisco as well as long as the HP is doing DHCP snooping. This prevents the Cisco from having to keep entries in the binding table on that port, which can be a consideration if you have many down stream clients and a switch with limited resources. – YLearn Aug 12 '13 at 17:49
-
Port 24 of the Cisco isn't Trusted. Port 24 of the HP is. – rsebastian Aug 12 '13 at 18:24
-
Did any answer help you? if so, you should accept the answer so that the question doesn't keep popping up forever, looking for an answer. Alternatively, you could post and accept your own answer. – Ron Maupin Jan 03 '21 at 22:10
1 Answers
11
DHCP snooping works by inspecting DHCP packets and dropping any such packet received on an untrusted port that is of a type sent by a DHCP server (most often OFFER, ACK and NACK).
The reason that you don't need to trust an AP port is that you should only be receiving client types of DHCP traffic on that port. While you receive DISCOVERY, REQUEST and INFO packets, you should not be receiving any OFFER, ACK or NACK packets on the AP port.
The caveat to this is that if you are using the AP as a bridge for a redundant path, then you would need to trust the port. If the primary link were to fail, then you would be passing DHCP server traffic back down to clients through the AP.
YLearn
- 27,141
- 5
- 59
- 128