How do people handle the need to add VLANs to all switches on their network (or even a subset of devices)? We are adding around 6 new VLANs per week at the moment and as the network grows this is becoming a very cumbersome and risky task.
10 Answers
Here is a really basic script template in Perl for telneting into a list of devices (one on each line in a file called devicelist.txt) and configuring some commands. Depending on exactly what you are doing it should provide a good start.
use Net::Telnet::Cisco;
# read in a list of devices
my @devicelist;
open(DATA, "<devicelist.txt") || die "Can't open file!";
while (<DATA>) {
chomp;
push( @devicelist, $_);
}
# loop through the devices
foreach $hostname (@devicelist)
{
# telnet to device
my $cs = Net::Telnet::Cisco->new(Host => $hostname);
# login, go enable, disable paging, go into config mode
$cs->login( "username", "password" );
$cs->enable( "enable_password" );
$cs->cmd( 'terminal length 0' );
$cs->cmd( 'config t' );
# configure the device
$cs->cmd( 'vlan 100, 200, 300' );
$cs->cmd( 'interface Ethernet0' );
$cs->cmd( ' switchport access vlan 100' );
# exit config mode and write the config
$cs->cmd( 'end' );
$cs->cmd( 'wr mem' );
# close the connection
$cs->close;
}
Here are some more details on Net::Telnet::Cisco as well.
- 2,057
- 1
- 14
- 26
-
4My only caution here is a pretty obvious one. This uses telnet and sends your passwords across the network in plain text. Would suggest using SSH. – bigmstone May 14 '13 at 20:00
I would say you have a couple of options:
- Manually. Takes most time. Safest? Depends on the one doing the config.
- Use some tool like Kiwi Cattools or Rancid etc. Much easier but you would need some kind of logic to check if VLAN is already existing or you could mess up the naming structure. Maybe not a huge deal?
- Script it! Use Perl, Python, Ruby or whatever language you have experience with. Takes some time to build it but once it done you could reuse script for other configuration tasks. It would be customizable but it depends on if you are comfortable coding.
- Use SNMP. Never tried this. Would require RW on the devices and I don't really like running RW on my network devices.
- 7,478
- 34
- 59
-
Do you have any examples of it being done scripted? Also I thought Rancid was just for reading, not modifying? – SimonJGreen May 13 '13 at 22:12
-
2I built a tool a while back in Python for running commands against multiple devices with expect. It takes two CSV files as arguments. One with commands, one with hosts. Can be found at http://matthewstone.net/2013/03/easyexpect/ I'm also working on a much more massive tool that's the child of EasyExpect called ZeroCLI. Not done yet, but putting it here for completeness. https://github.com/mstone7699/ZeroCLI – bigmstone May 13 '13 at 22:34
-
1Rancid is for retrieving but it also comes with clogin and you can use that to automate logins to devices. It also takes a file as argument where you can put commands that should be entered. – Daniel Dib May 14 '13 at 05:45
Configuration management software might be worth looking into -- Puppet's network device management can add vlans easily to numerous Cisco devices (if you're using Cisco).
- 615
- 5
- 15
-
2Juniper also started a puppet agent (https://github.com/Juniper/puppet-netdev-stdlib-junos) – Jan-Philipp May 14 '13 at 14:15
The challenge you now face is that you are going into a mixed environment. You mention you are moving towards Juniper from I assume Cisco? In a pure Cisco environment VTP v3 with passwords would be the way to go and supports over 4k vlans. In the Juniper world the equivalent would be GVRP.
You may be able to use some form of centralized management such as Puppet as was mentioned by Shane Madden, SolarWinds, HP OpenView and such but you will still have two scripts to manage.
I would try to keep things as simple as possible (KISS) for now as you transition from one vendor to another. Using VTP and GVRP on the appropriate hardware is probably the way to go and doesn't add the potential cost for other solutions or complexity of managing another new thing.
- 1,351
- 12
- 28
It could be that VTP is your answer. Like any "automated" tool, it has it's risks, but you can mitigate them with proper planning. You should also do some reading to make sure you understand how it works or you can inadvertently create your own problems (again, just like any automated tool).
I would recommend VTP version 3, as this can help protect from some of the potential problems and provides additional benefits.
You can easily find hundreds of documents by searching "vtp version 3 configuration" in your search engine of choice.
- 27,141
- 5
- 59
- 128
-
Unfortunately we hit the 200 VLAN limit on VTP a while ago. We've also started to move to Juniper. – SimonJGreen May 14 '13 at 06:30
-
-
1I have never heard of a VTP 200 VLAN limit, and we are doig over 200 VLANs through VTP. I would definately like to hear more about what you mean. VTP version 1 and 2 are limited to only using VLANs 1-1001 as specified by ISL, but VTP version 3 goes up to the dot1Q 4095. There is a limit to the number of local VLANs a switch can support, but you can't violate this locally even in tansparent mode. – YLearn May 14 '13 at 12:09
-
1
-
@Jan-Philipp, would you please explain your statement, instead of just saying "it's risky"? *Why* is it risky, IYO? – pboin May 14 '13 at 15:41
-
even if there is a password applied, if you repower an old switch witch vtp config applied and connect it to the vtp domain its possible that this switch has a higher revision then the vtp and removes a buch of vlans. – Jan-Philipp May 14 '13 at 16:00
-
You have to be careful with VTP if you have more VLANs than the amount of spanning-tree instances supported by the lowest common denominator switch in the network. For example if you don't prune VLANs on the uplinks (either on purpose or by accident), you can have a switch in your network that has some VLANs without spanning-tree enabled. – Snowscan May 14 '13 at 16:37
-
While, yes, VTP will allow you to automate VLAN creation it is only relevant in each L2 domain and is vendor specific. For those reasons I feel like this answer is not valid given the original question, "How do people handle the need to add VLANs to all switches on their network..." This implies crossing L3 boundaries...which VTP does not. – bigmstone May 14 '13 at 16:43
-
@Jan-Philipp, I would say no more risky than any other automated tool used by someone who doesn't understand it and take the proper precautions. I often hear your reason touted as a problem with VTP, but if you have a prolicy of not using the production VTP domain on any non-production switch, you should never have a switch in VTP server mode with a higher revision number added to the network (plus you should be ensuring any switch is NOT in VTP server mode when adding to a production network). – YLearn May 14 '13 at 22:10
-
@Snowscan, your statement is true whether you use VTP, an automated tool or manually apply VLANs to a switch in transparent mode. – YLearn May 14 '13 at 22:13
-
@bigmstone, first off, the question does not imply at all that there is any crossing of L3 boundries. There are very large networks that are largely L2. Second, yes, VTP is Cisco centric. If you want a standard based option, you can go wtih GVRP or MVRP. – YLearn May 14 '13 at 22:21
-
@YLearn no, if you propagate vlans via a provision script the risk of human errors will be lower even without sanity checks – Jan-Philipp May 15 '13 at 07:23
-
@Jan-Philipp, that is your opinion. I knew a network admin who worked on a network with 300+ switches, a provision script and no VTP. While cleaning up their VLANs, he accidentally fat fingered entering the list of VLANs to remove and removed the management VLAN from the database and the VLAN allowed list on switch interconeccts. This affected about 70% of the network. With VTP and automatic pruning, you could fix this by simply re-adding the VLAN. In that case, they had to physical visit around 200 switches to restore service. – YLearn May 15 '13 at 12:41
Solarwind's Network Configuration Manager can run scripts in IOS devices and some others.
It also does things like nightly config backups, change reports and config audits. Their pricing isn't horrible but they're merging NCM with their Orion Network Performance Monitor and I'm not certain you can run NCM separately any more.
- 1,351
- 12
- 28
- 950
- 7
- 16
-
I believe that NCM is still being offered as a standalone product but it is becoming more integrated with NPM with each new release. If you have a large environment, NCM is worth its weight just for the backup and configuration change reporting. – harrijs May 14 '13 at 03:43
It sounds like you have a collapsed core. Is that correct?
One way of dealing with too many changes based on adding new VLANs' is to move your L3 boundary closer to the access. It requires some work up-front, but if your design is well planned, and thought out, it should make adding new VLAN's a one to three device task (depending on whether L3 stops at Distribution or Access layers).
There are a bunch of other benefits you get from that as well, including faster convergence in the event of a lost link.
- 29,876
- 11
- 78
- 152
- 416
- 2
- 4
I use ruby with the net-scp and net-ssh gems to automate tasks with our network equipment. It's a pretty short script to execute commands (excerpt, not a finished product):
begin
Net::SSH.start(fqdn, username, :password => loginPassword) do |session|
output = ""
channel = session.open_channel do |ch|
ch.send_channel_request "shell"
ch.on_data do |ch, data|
output += data
end
ch.send_data "conf t\n\r"
#Some tasks here
ch.send_data "exit\n\r" #Exit config mode
ch.send_data "exit\n\r" #Exit device
end
# Wait for everything to complete
channel.wait
end
rescue Exception=>e
errorOutput = fqdn + ": " + e.to_s
puts errorOutput
puts output
return device
end
return output
Keep in mind that you should have a blank loginPassword variable. If blank, it will use your RSA public key for login (supported on HP ProCurve and Cisco 15.X platforms).
Using something like git and a few short scripts, you can organize all your equipment configurations with diffs of changes and who made the changes (assuming your engineers pull configs and commit them after work is completed).
Also it should go without saying, but just in case, always test scripted work in a lab before running on production equipment. Especially when executing commands and changing configurations. Test, test, test.
- 3,052
- 1
- 19
- 30
if you use the same constructor(Cisco for example) for your network devices, SecureCRT is your best choice. it is an SSH client that give you the possibility to send commands at multiple terminals at the sale time:
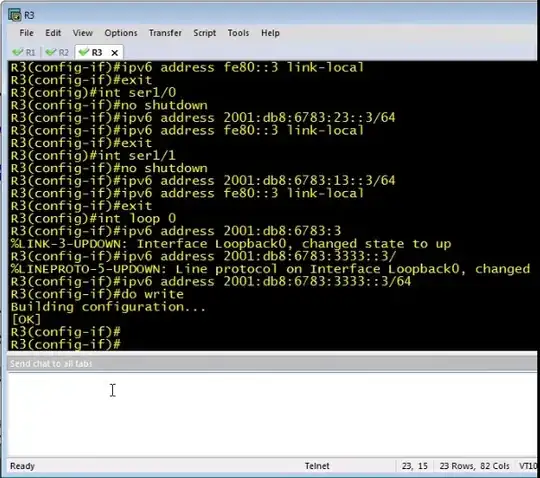
to set that up: 1. connect to all your devices in different tabs 2. go to view 3. check "chat window" option 4. right click on the window -> check "send chat to all tabs"
- 33
- 2
Use may use NOC, NOC Project it's the scalable, high-performance and open-source OSS system for ISP. You can easily add VLAN's through the entire network.
- 710
- 6
- 8