today I found out that somebody in our organization utilized our uplink for 100%. We have Cisco WLC 2500 where I could see in application monitoring that 80% traffic of the last 90 sec was a file hosting service traffic. So, somebody had been downloading some big file. I will try to configure QoS for bandwith limitation but here is a question - how can I find in real-time who utilizes the bandwith?
-
1The alternative way to identifying the individual by inspecting traffic is to block the traffic and listen out for the user who complains about the Internet being broken. (only works if the file hosting service is not crucial to the company's operation. Don't actually do this, it's a joke) – stefan Mar 13 '20 at 08:09
3 Answers
The easy way to do it could be:
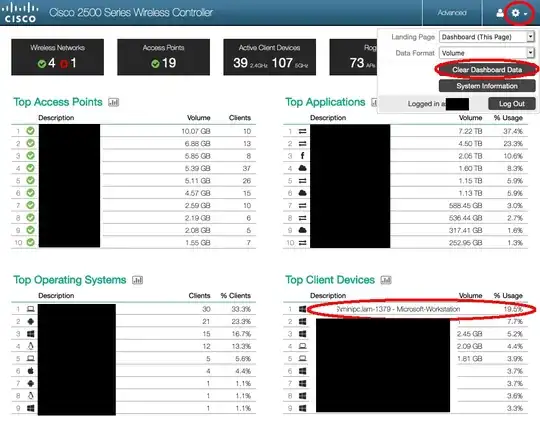
On your WLC home page you should have something like:
You can reset the stat through the gear icon on the top right corner, selecting "Clear Dashboard Data"
Then the machine should quickly appear in the "Top Client Devices" list, you can click on it and you will get the IP address and the mac address of the device.
Bonus if you use Radius / NPA authentication, you could see directly the user which is authenticated on the device.
- 19,405
- 1
- 32
- 64
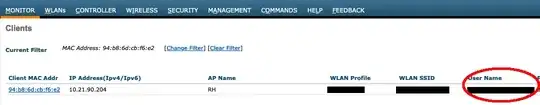
The WLC will tell you the MAC address of the client, and the AP it's associated to. Netflow is another option.
- 66,852
- 5
- 65
- 126
-
Where I can find MAC of the client who utilizes the link? Under Monitor > Applications > WLAN I can see only the statistics, what app is using more bandwidth but not WHO is using that – dtsn Mar 12 '20 at 12:23
Unlike IP addresses, that are often dynamically allocated, MAC addresses are unique identifiers that can be used to reliably identify hosts in your network. Flexible NetFlow allows collecting VLAN IDs or MAC addresses. https://www.noction.com/blog/finding-mac-addresses-using-flexible-netflow
- 11
- 1
-
Hi and welcome to Network Engineering! It's generally helpful to quote the relevant part of the document you link to, since links tend to go stale after some time. That way, later readers can still get the gist of what you're suggesting. – Ron Trunk Mar 12 '20 at 13:08
-
3"_MAC addresses are unique identifiers that can be used to reliably identify hosts in your network._" That simply is not true. MAC addresses need to be unique in a LAN, but they are easily changed, so they are not reliable for host identification. Fools rely on MAC addresses for things like security, thinking they are a reliable way to identify a host on the LAN. – Ron Maupin Mar 12 '20 at 13:52
-
When's the last time you saw someone change their MAC? (Apple does this for you in some cases "for enhanced privacy") – Ricky Mar 12 '20 at 15:26
-
6@RickyBeam - "When's the last time you saw someone change their MAC?" - Infact Android 10 and some linux distros have this set as the default to automatically cycle MACs for privacy purposes – Milney Mar 12 '20 at 17:10