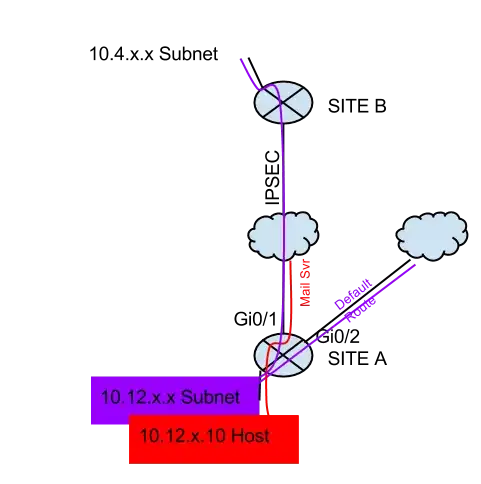
Ive got 2 sites with an IPSEC connection between them. Each site has a 2921 on the edge.
Site A 2921 (gi0/1) ---> <--- (gi0/1) 2921 Site B
I am adding a second WAN connection to site A via the third interface on the 2921 (gi0/2).
10.12.x.x Site A 2921 (gi0/1) ---> <--- (gi0/1) 2921 Site B 10.4.x.x
Site A 2921 (gi0/2) ---> 0.0.0.0
Ideally I would like to use PBR to send users behind Site A's 2921 out the gi0/2 interface unless they are destined for an address in Site B. I am also hosting a mail server from Site A on the gi0/1 interface's IP address.
I've done PBR before, but the VPN (I think) is throwing in some complexities for me.
When I set the interface overload commands and apply the route map to the interface, it just stops working. If I just remove the PBR and set gi0/1 back to the default route, everything works just fine.
Thanks for the help!
Site A Configuration
interface GigabitEthernet0/0
description Inside
ip address 10.12.x.x 255.255.255.0
no ip redirects
no ip proxy-arp
ip policy route-map internet
ip nbar protocol-discovery
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
no mop enabled
interface GigabitEthernet0/1
description TO SITE B
ip address a.a.a.a 255.255.255.0
no ip redirects
no ip proxy-arp
ip accounting access-violations
ip verify unicast source reachable-via rx allow-default 100
ip nbar protocol-discovery
ip flow ingress
ip nat outside
ip inspect OutsideFirewall out
ip virtual-reassembly in
duplex auto
speed auto
no cdp enable
no mop enabled
crypto map S2S_VPN
interface GigabitEthernet0/2
description TO 0.0.0.0
ip address dhcp
no ip redirects
no ip unreachables
no ip proxy-arp
ip accounting access-violations
ip verify unicast source reachable-via rx allow-default 100
ip nbar protocol-discovery
ip flow ingress
ip nat outside
ip inspect OutsideFirewall out
ip virtual-reassembly in
duplex auto
speed auto
no cdp enable
no mop enabled
ip nat inside source route-map NAT interface GigabitEthernet0/1 overload
ip nat inside source static tcp 10.12.x.10 80 interface GigabitEthernet0/1 80
ip nat inside source static tcp 10.12.x.10 995 interface GigabitEthernet0/1 995
ip nat inside source static tcp 10.12.x.10 25 interface GigabitEthernet0/1 25
ip nat inside source static tcp 10.12.x.10 443 interface GigabitEthernet0/1 443
ip nat inside source list NAT interface GigabitEthernet0/2 overload
ip route 0.0.0.0 0.0.0.0 192.x.x.x (gi0/2 gateway)
ip access-list extended NAT
deny ip any 10.4.x.x 0.0.0.255
permit ip any any
ip access-list extended to_gi01
permit ip 10.12.x.10 0.0.0.0 any
permit ip 10.12.x.x 0.0.0.255 10.4.x.x 0.0.0.255
deny ip any any
route-map internet permit 10
match ip address to_gi01
set ip next-hop a.a.a.a (gi0/1 gateway)
Site A Crypto Section
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto ipsec transform-set S2S_SET esp-3des esp-md5-hmac
mode tunnel
crypto isakmp key blahblah address x.siteB.x.x
crypto map S2S_VPN 1 ipsec-isakmp
description S2S VPN
set peer x.siteB.x.x
set transform-set S2S_SET
set pfs group1
match address siteB_ACL
ip access-list extended siteB_ACL
permit ip 10.12.x.0 0.0.0.255 10.4.x.0 0.0.0.255
Simple Network Drawing